|
◆
What is IPsec?
IPsec,Encryption systemUsed to protect the security of data at the network layer by the technology
It is a protocol to be done. IPsec consists of protocols such as AH, ESP, and IKE. This IPsec
By using the VPN connection we can communicate safely even in the public infrastructure such as the Internet.
◆IPsec works layer
Since IPsec operates at the network layer, whether it is TCP or UDP at the transport layer which is the upper layer
It works without problems, and there is no limit, so it does not depend on a specific application. However, the network layer
IP
It must be. By the way, it has nothing to do with IPsec, but SSL works at the session layer. And
The network layerIP, The transport layerTCPIt must be. For this reason all TCP / IP
Applications such as “HTTP / FTP / SMTP” can be used, but UDP applications can not be used.
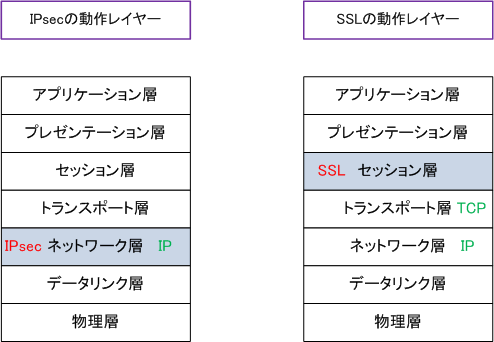
* SSL works exactly at the boundary between the transport layer and the session layer.
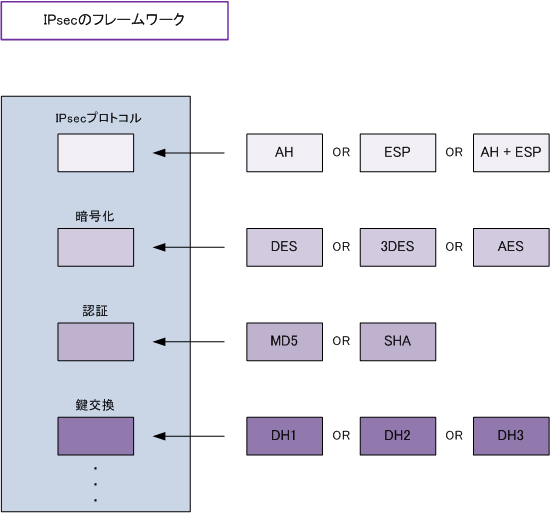
◆Two protocols constituting IPsec and a key exchange protocol
IPsec itself, as its name implies, is a security architecture. IPsecAH,ESP,IKESuch as multiple
It consists of protocols. AH stands for “Authentication Header”, and as its name implies, authentication function
I have. ESP is an abbreviation for “Encapsulated Security Payload”, and encryption is applied to the payload part
You can do it. IKE stands for “Internet Key Exchage” and is a protocol that can exchange keys.
| IPsec Protocol |
role |
Protocol type |
| AH |
· Authenticate whether the packet has not been tampered with. (HMAC)
· Packet encryption is not possible.
|
IP protocol number 51 |
| ESP |
· Authenticate whether the packet has not been tampered with. (HMAC)
· Perform encryption (DES or 3DES or AES) of the payload part of the packet.
|
IP protocol number 50 |
| IKE |
· Secure exchange of secret key information. IKE is [ISAKMP / Oakley].
In other words, it implements the Oakley key exchange procedure on the ISAKMP protocol.
· Diffie-Hellman key exchange algorithm is one of Oakley components.
|
UDP port number 500 |
For RFC 2406 and RFC 4303 format ESP
Authentication Trailer
There is a function. With this, without using AH together
It can prevent tampering. Therefore, IPsec can be configured with ESP and IKE alone without AH.
However, with the authentication trailer function of ESP, it is not possible to guarantee its integrity up to the IP header part.
Also, why ESP can implement AH even though ESP can implement all security services
AH is less loaded than ESP, AH has no export restrictions, AH is essential for IPv6 compliance.
* Current IPsec-VPN in Japan is IPsec-VPN only using “ESP and IKE” that does not use AH is a common implementation method.
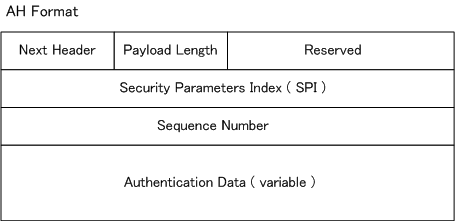
| AH fields |
Description of each field |
| Next Header |
A field indicating the type of protocol (such as TCP / UDP) that comes after AH. |
| Payload Length |
A field indicating the length of AH. |
| Reserved |
Fields reserved for the future. It is set to 0. |
| SPI |
A field indicating SA (Security Association) used for the packet |
| Sequence Number |
A field indicating the sequence number assigned to each packet. Package replay can be prevented by this. |
| Authentication Data |
A field indicating the HMAC value of that packet. The value is called ICV (Integrity Check Value). |
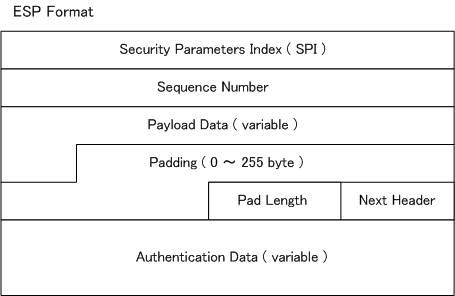
| ESP fields |
Description of each field |
| SPI |
A field indicating SA (Security Association) used for the packet |
| Sequence Number |
A field indicating the sequence number assigned to each packet. Package replay can be prevented by this. |
| Payload Data |
Variable length field containing data defined by Next Header field |
| Padding |
Adjustment field for adjusting the length of the payload data to the size required by the algorithm. |
| Pad Length |
Indicates the number of bytes in the Padding byte. |
| Next Header |
A field indicating the type of protocol (eg TCP / UDP) coming after ESP. |
|
|
|



